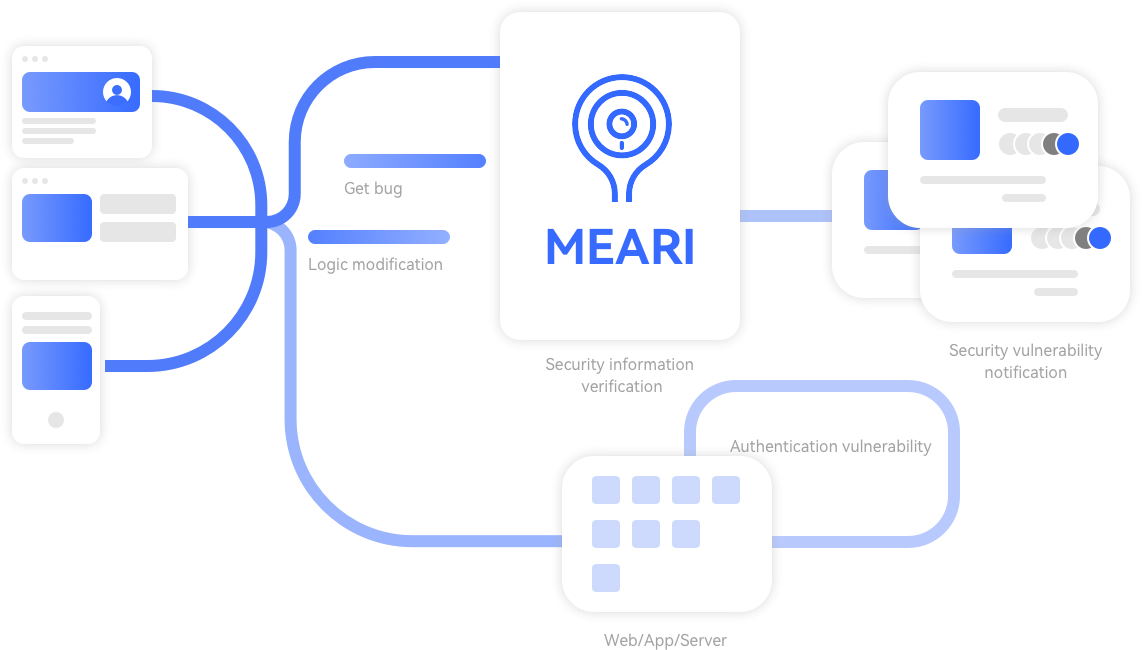
1.ReceiptReceiving and gathering reports of potential product security vulnerabilities

2.VerificationCoordinating with relevant teams to verify the vulnerability and conduct a risk assessment

3.RemediationAnalyzing the root cause of the vulnerability and implementing a fix

4.DisclosureProactively disclose vulnerability information and release fixed firmware

5.ImprovementEnhance vulnerability scanning capabilities and integrate them into product security requirements